2023 Blog, Cloud Blog, Blog, Featured
Currently, all large enterprises are dealing with multi-cloud providers and the situation is more complicated where M&A has led to multiple organizations integrations and multiple vendors across Infrastructure, Digital, Enterprise Systems, and Collaboration tools bring their own Cloud footprints bundled with services. In this blog, we try to explain the common scenario being faced by large companies and how to create “The Right Way” to adopt a scalable Multi-Cloud Workload Planning and Governance Models.
Customer Needs
The customers facing such challenges usually share with us the following brief:
- Assess existing workloads on AWS, Azure, GCP for basic health & maturity diagnostics.
- Suggest a mature Cloud Management & Governance model for ensuring “The Right Way” to use the Cloud for multi-account, secure, and compliant best practices.
- Recommend a model for future workloads migration and choice of cloud providers for optimal usage and ability to move new workloads to cloud easily.
Primary Business Drivers
Following are the key reasons for customers seeking Multi-Cloud Governance “The Right Way.”
- Cost optimization and tracking for existing usage.
- Ability to launch new regions/countries in cloud with easy and secure standardized processes.
- Bring down cost of ownership on Cloud Assets – Infra/Apps/Managed Services with leverage of Automation and best practices.
Approach Taken
The basic approach followed for helping customers through the multi-cloud maturity models involves a PLAN-BUILD-RUN process as explained below:
Step-1: Planning & Assessment Phase
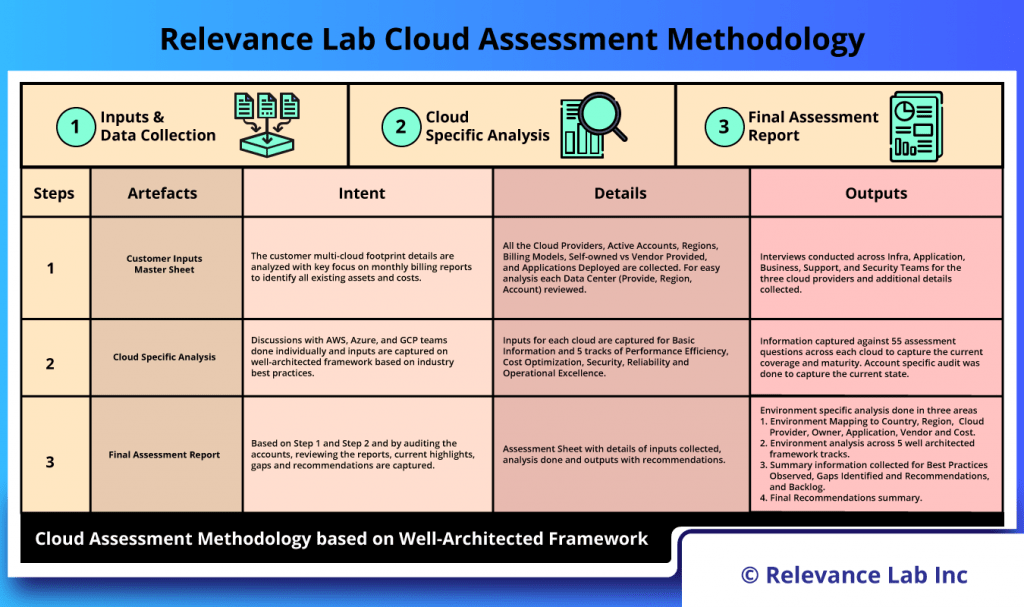
This involves working with customer teams to finalize the Architecture, Scope, Integration and Validation Needs for Cloud Assessment. The primary activities covered under this phase are following:
- Coverage Analysis
- Do a detailed analysis of all three Cloud Providers (AWS, Azure, GCP) and recommend what should be an ongoing strategy for Cloud Provider adoption.
- Maturity Analysis
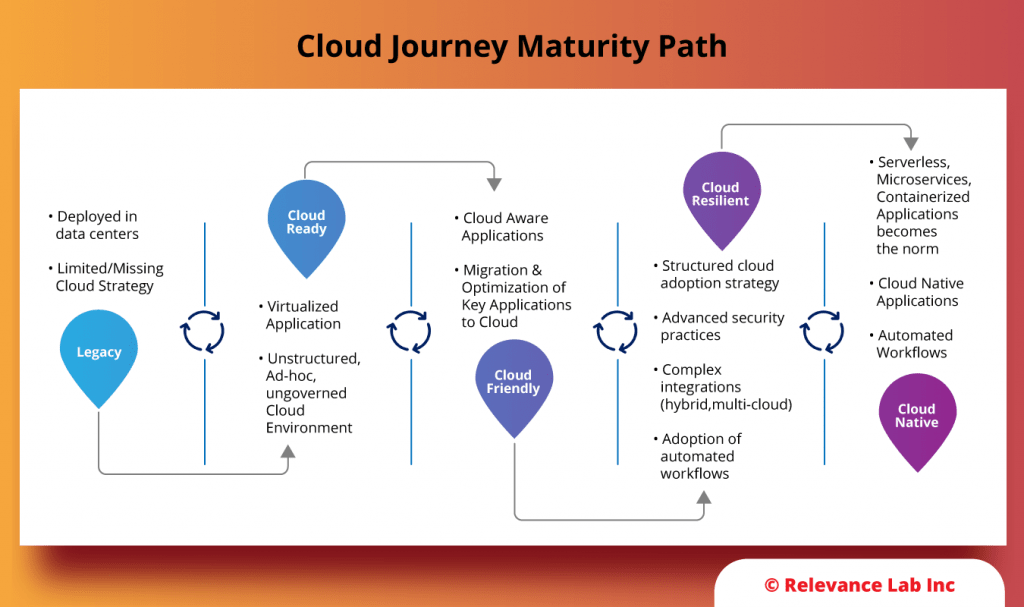
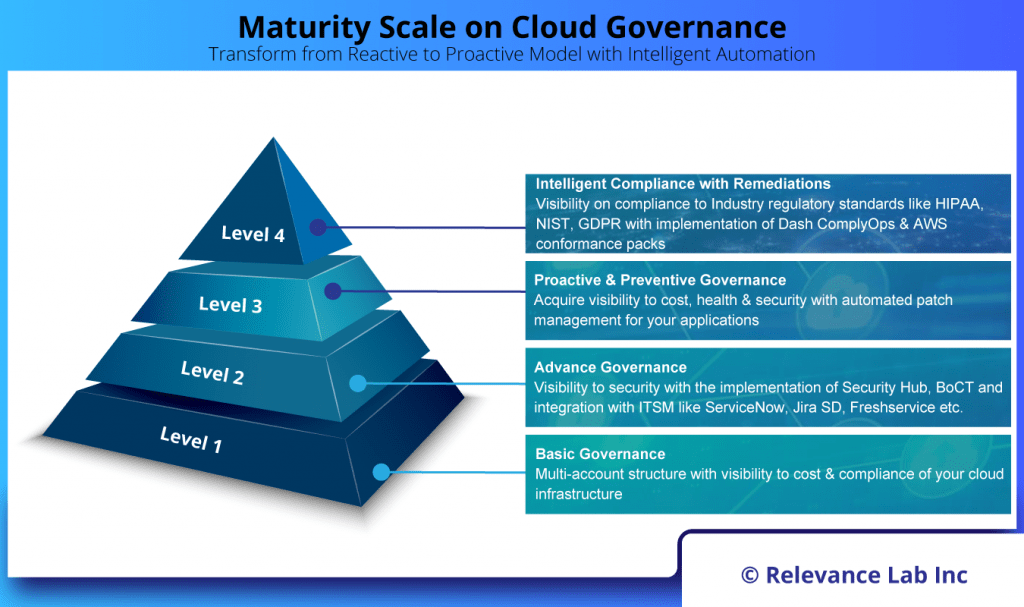
- Do an assessment of current Cloud usage against industry best practices and share the maturity scorecard of customer setup.
- Security Exposure
- Find key gaps on security exposure and suggest ways for better governance.
- Cost Assessment
- Consolidation and cost optimization to have more efficient cloud adoption.
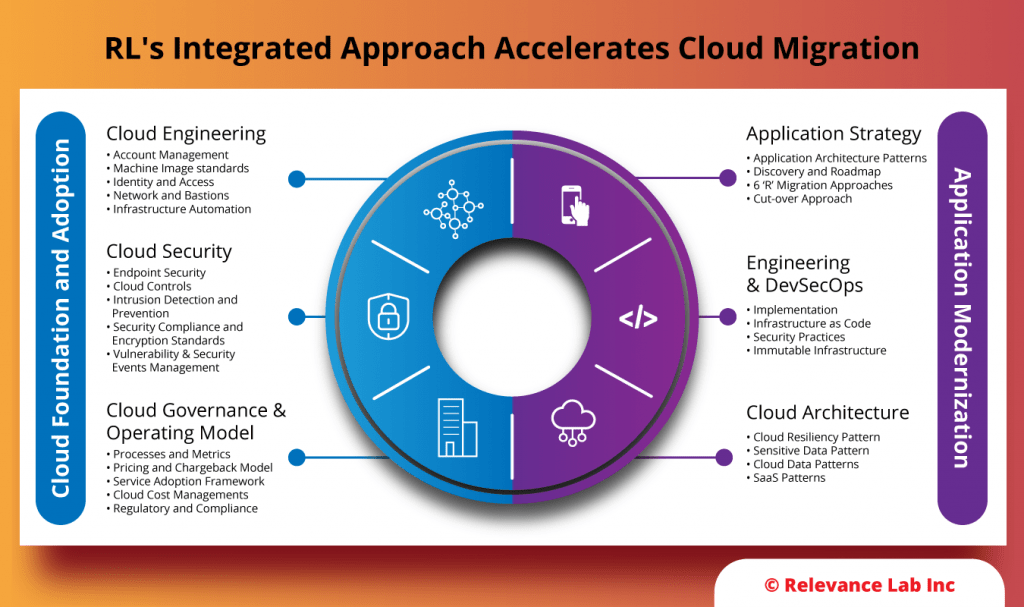
The foundation for analysis covers Cloud Provider specific analysis based on Well-Architected Frameworks as explained in the figure below:
Step-2: Build & Operationalize Phase
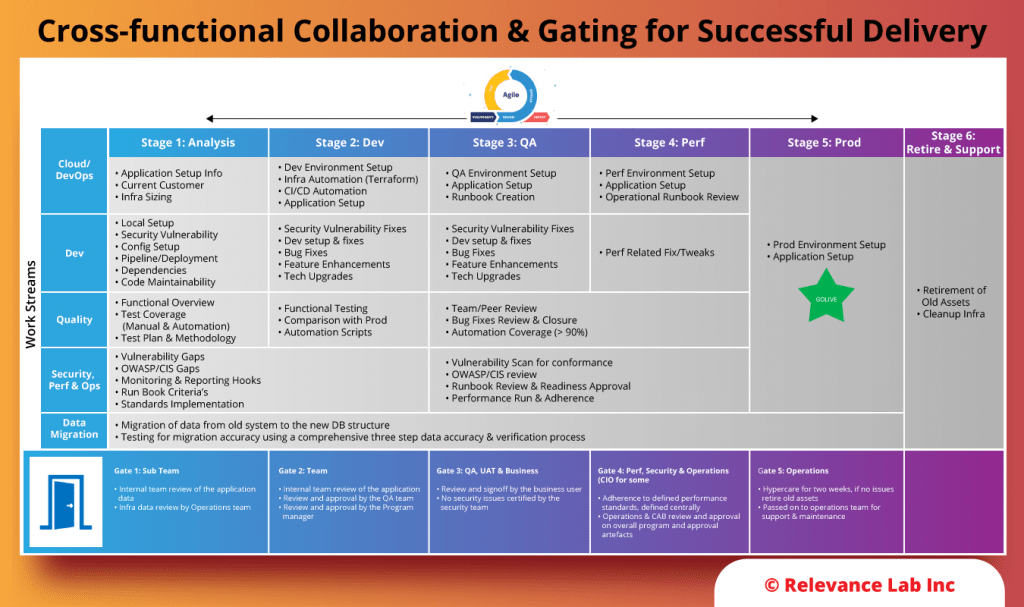
This primarily involves adoption of mature Cloud Governance360 and Well-Architected Models with best practices across key areas.
- Accounts & Organization Units
- Guardrails
- Workloads Migration
- Monitoring, Testing, Go-Live & Training
- Documentation, Basic Automation for Infrastructure as Code
- SAML Integration
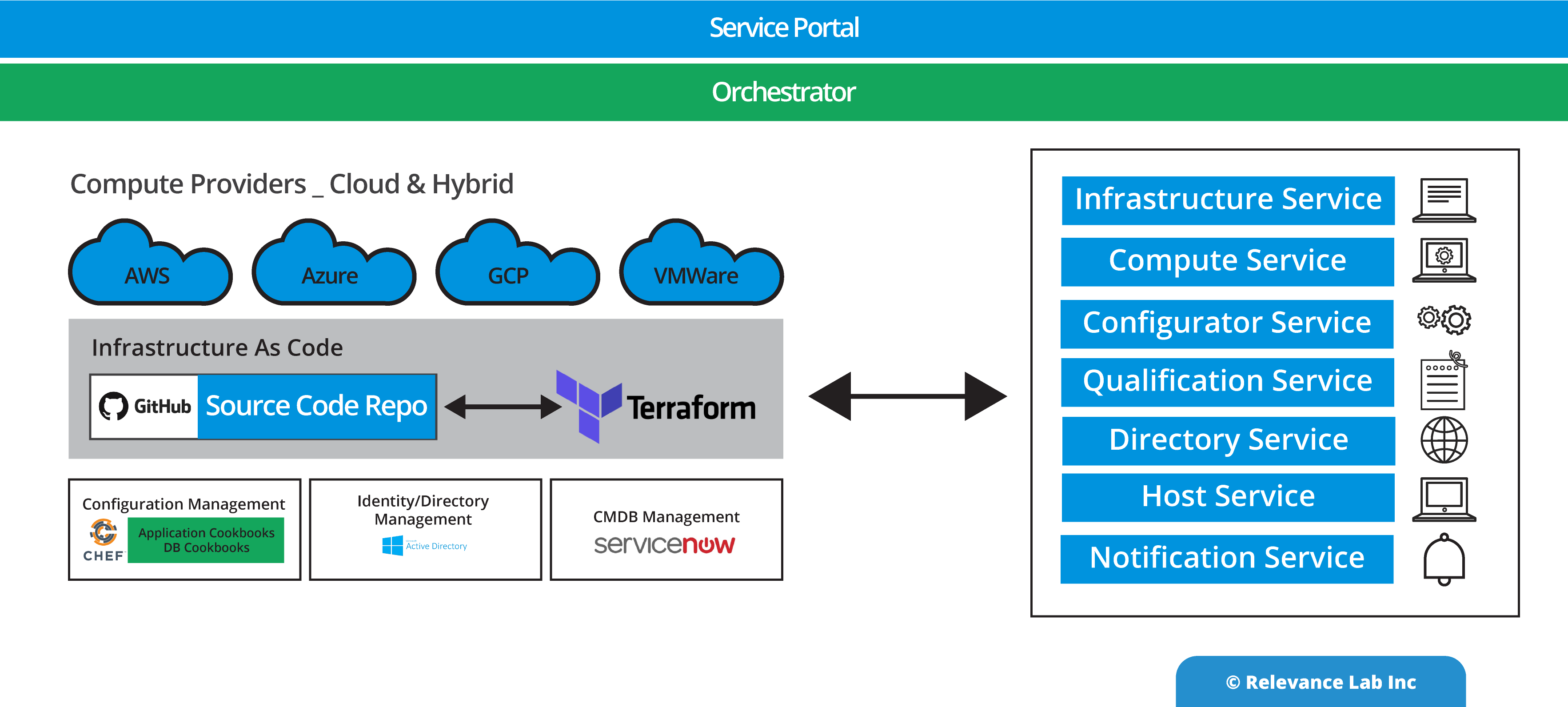
The playbook for Build & Operationalize phase is based on Relevance Lab prescriptive model for using Cloud “The Right Way” as explained in the figure below.
Step-3: Ongoing Managed Services Run Phase
Post go-live on-going managed services ensure that the best practices created as part of foundation are implemented and “Automation-First” approach is used for Infrastructure, Governance, Security, Cost Tracking and Proactive Monitoring. Common activities under Run phase cover regular tasks a snapshot of what is provided below:
Daily Activities:
- Monitoring & Reporting – App & Infra using CloudWatch – Availability, CPU, Memory, Disk Space, Security blocked requests details, Cost using Cost Explorer.
- Alert acknowledgement and Incident handling.
- Publish daily report.
Weekly Activities:
- Check Scan Reports for most recent critical vulnerabilities.
- Monitor Security Hub for any new critical non-compliances.
- Plan of action to address the same.
Monthly Activities:
- Patch Management.
- Budgets Vs Costs Report.
- Clean-up of stale/inactive users/accounts.
- Monthly Metrics.
ServiceOne framework from Relevance Lab provides a mature Managed Services Model.
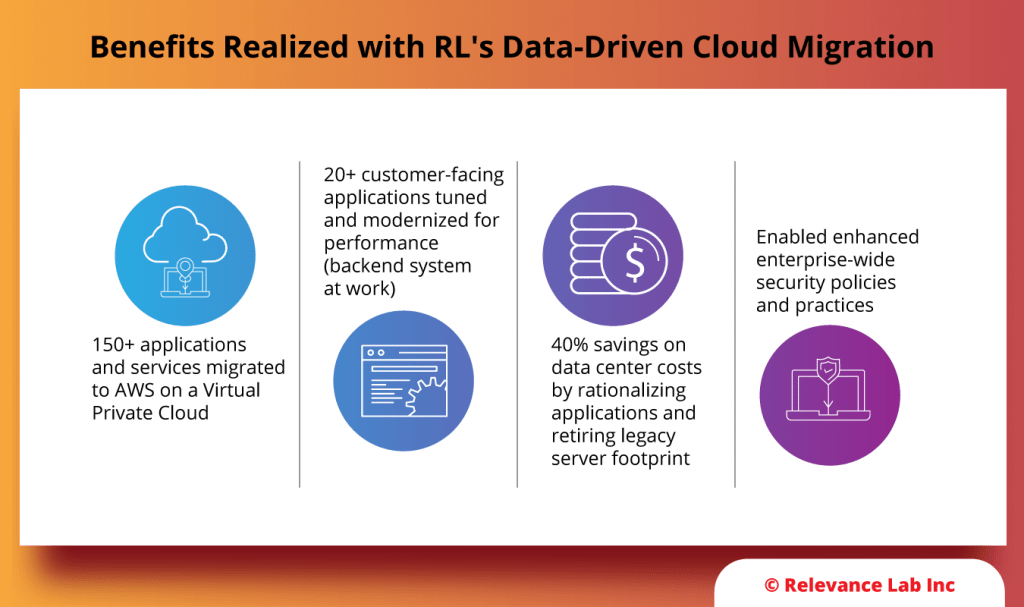
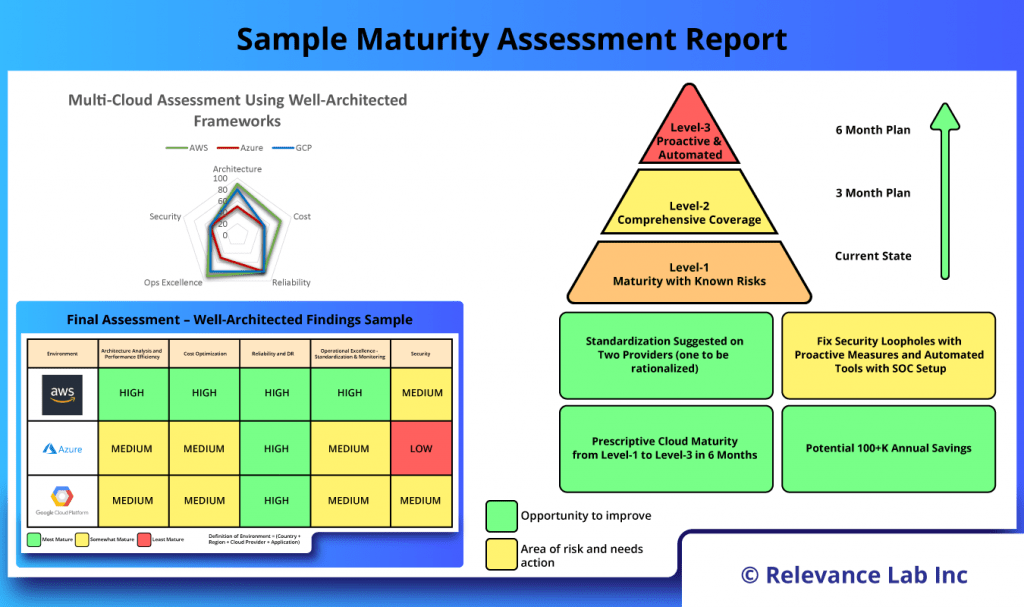
Sample Assessment Report
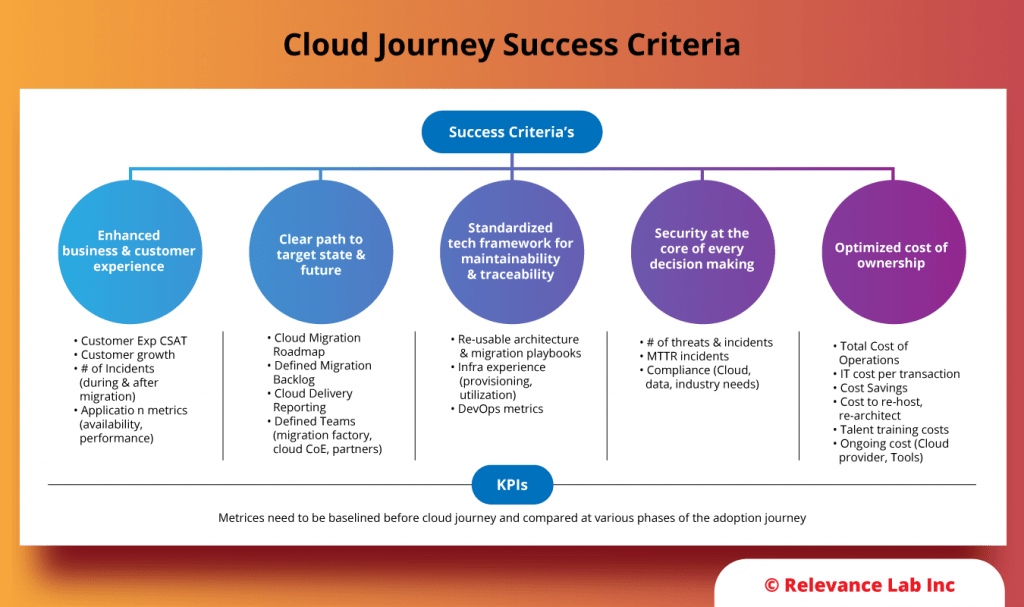
The analysis is done across 4 key areas as covered under Plan phase and explained below.
- Cloud Provider Specific Analysis
- Workload distribution analysis across all three providers, also mapped to 50+ different Best Practices Questionnaire.
- 5-Pillars Well-Architected Analysis
- Architecture & Performance Efficiency, Cost Optimization, Reliability & DR, Operational Excellence & Standardization, Security.
- Global workloads analyzed across all different environments.
- Security Findings
- Identified Environments on Azure with significant exposure that needs fix.
- Also suggested AWS Security Hub for formal scorecard and specific steps for maturity.
- Cost Optimization
- Analyzed costs across Environments, Workloads, and Apps.
Based on the above a final Assessment report is created with recommendations to fix immediate issues while also addressing medium term changes for ongoing maturity. The figure below shows a sample assessment report.
Summary
Relevance Lab is a specialist company in cloud adoption and workload planning. Working with 50+ customers on multiple engagements, we have created a mature framework for Multi-Cloud Workload and Governance Assessment. It is built on the foundation of best practices for Cloud Adoption Framework (CAF) and Well-Architected Frameworks (WAF) but enhanced with specific learnings and accelerators based on Goverenance360 and ServiceOne offerings to speed up a transition from un-managed & ad-hoc models to “The Right Way” of multi-cloud foundation.
To know more on how we can help feel free to contact us at marketing@relevancelab.com
References
AWS Well-Architected
Microsoft Azure Well-Architected Framework
Google Cloud Architecture Framework
AWS Cloud Adoption Framework (AWS CAF)
Microsoft Cloud Adoption Framework for Azure
Google Cloud Adoption Framework