AWS Service Management Connector for Jira Service Desk to provision and maintain AWS resources for User On-boarding with RLCatalyst Intelligent Automation.
Click here for the full story.
2020 Blog, Blog, Featured
As enterprises adopt popular Agile and DevOps tools and solutions from Atlassian, it is essential to create an end to end automation pipeline covering ITSM workflows. Integration of Software Development Lifecycle (SDLC) tools, with cloud infrastructure platforms like AWS, can provide faster software deliveries with CI/CD, infrastructure automation and continuous production monitoring. RLCatalyst Intelligent Automation solutions complement the platform with an enterprise BOTs Automation solution and a mature end-to-end monitoring Command Centre solution. This blog details out an integrated solution between AWS Service Management Connector for Jira Service Desk enterprise workflows of User Onboarding + Asset Provisioning lifecycle.
The AWS Service Management Connector for Jira Service Desk (Jira SD) allows Jira Service Desk end-users to provision, manage, and operate AWS resources natively via Atlassian’s Jira Service Desk. Jira Service Desk Cloud module supports AWS Service Catalog Connector, and the Jira Service Desk Data Centre & Server module supports AWS Service Management Connector.
Jira SD admins can create and provide secured, governed AWS resources to end-users via service catalog, execute automation playbooks via AWS system manager and finally track the resources in a Config Item view powered by AWS config.
On downloading the connector from the Atlassian marketplace for no additional cost, you need to connect it with your AWS account, preferably governed by AWS Control Tower for enhanced security.
The AWS Service Catalog allows you to provision or terminate and centrally manage commonly deployed AWS resources like workspaces. AWS resources like workspaces can be pre-approved, provisioned or terminated based on approval.
Similarly, the AWS Service Management Connector allows Jira SD users to fulfil all the related operational activities. Some of them are listed below.
- Migrate or Manage CloudWatch Agent.
- Manage Amazon Inspector Agent.
- Apply Ansible Playbooks or Chef Recipes on AWS managed instances.
- Apply Patches from baseline.
- Change the standby state of an EC2 instance in an auto-scaling group.
- Attach an additional EBS Volume to the EC2 instance.
- Attach IAM to an Instance.
- Install or Uninstall a Distributor package.
- Configure CloudTrail Logging.
- Export Metrics and log files from your instances to Amazon CloudWatch.
- Configure an instance to work with containers and Dockers.
- Enable or disable live patching on Linux EC2 instances.
- Configure S3 bucket logging.
- Enable or disable Windows Updates.
- Copy Snapshot created.
- Create DynamoDB backup.
- Create a new AMI from an EC2 instance.
- Create an RDS snapshot for an RDS instance.
- Create an incident in ServiceNow.
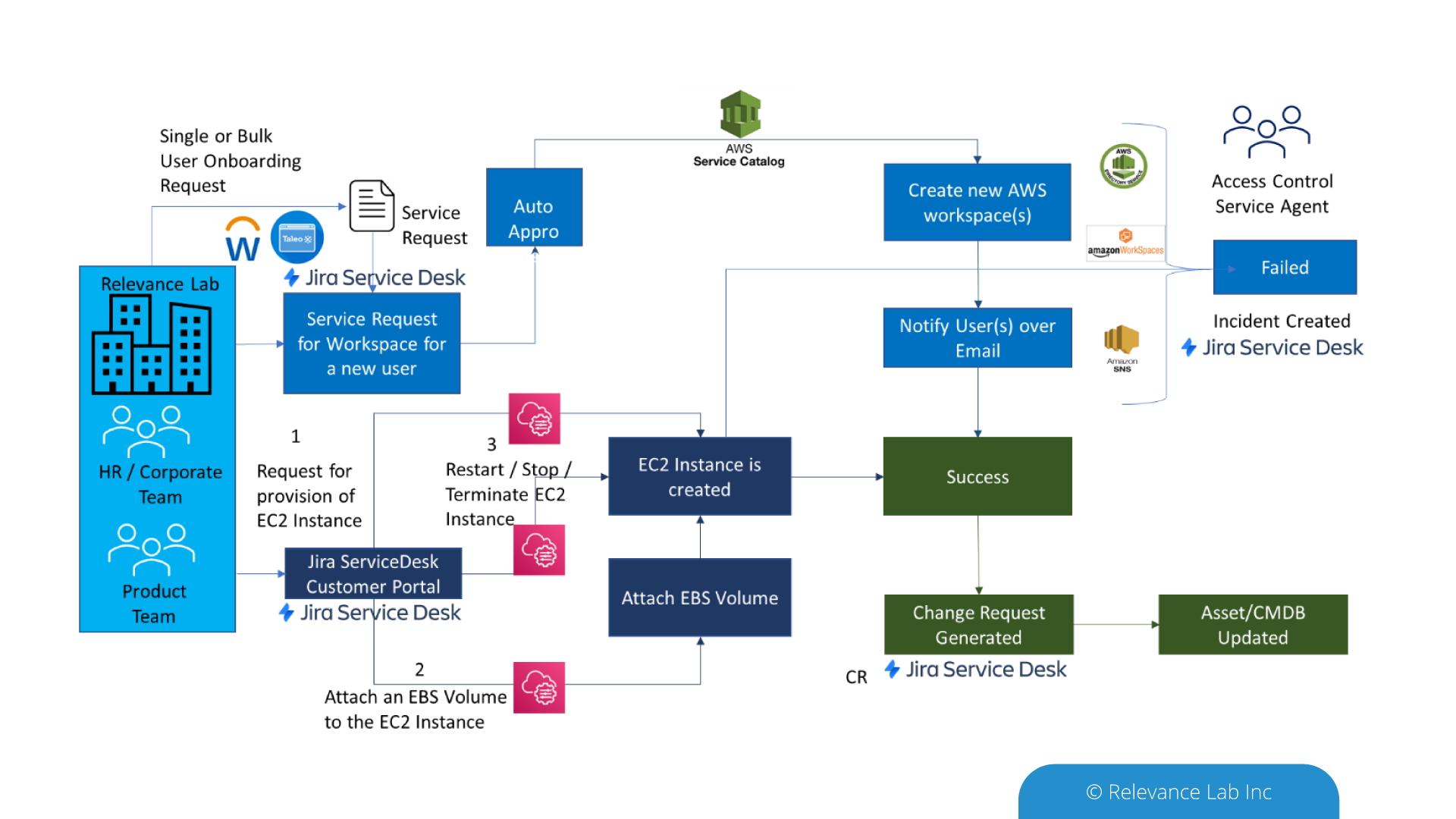
As shown in the above diagram, Relevance Lab helps enterprises already on AWS & Jira Service Desk, to integrate the two using AWS Service Management Connector. The integration enables a seamless process to create custom workflows like the creation of auto-approval, cost-based approval and role-based approval. Likewise, raise an incident in case of any failure of the resources provisioned or terminated and create change requests for every update of the workloads.
Benefits of AWS Service Management Connector for Jira Service Desk:
- Free and Out of Box (OOB) feature without any add-on cost.
- Support multiple AWS accounts and ensure governance through AWS CT.
- Provision and Maintenance of AWS resources through one platform (Jira SD).
- Easy to use by the IT admins without in-depth knowledge of AWS platform.
- Multiple Portfolios and Service Catalogs for different departments within an Organization.
- Represent Config Items in a tree structure.
- Run most of the automated documents in AWS system manager through Jira SD.
The end to end orchestration of User Onboarding and Asset provisioning leverages the out of box features for AWS and Atlassian tools. However, for many real-world scenarios, the complex workflows need integration with other third-party tools like AD, OKTA, HR systems (Workday/Taleo) and compliance solutions. In situations that require more complex workflows and third-party integrations RLCatalyst BOTs solution is integrated with AWS and Atlassian solutions to provide lifecycle automation and observability post provisioning.
Conclusion:
Relevance Lab is a partner of AWS and a DevOps specialist company implementing Atlassian solutions. We help organizations adopt AWS Service Management Connector with ITSM tools like Jira Service Desk and ServiceNow. Integration of AWS Service Management Connector provides a common interface and ease for all L1 and L2 activities for the ITSM users to manage AWS resources. Our RLCatalyst based Intelligent Automation and Command Centre complement these solutions to bring in greater efficiencies.
Click here for a demo video.
For more details, please feel free to reach out to
marketing@relevancelab.com
SOX Compliance is an essential part of large enterprises governance process. Leveraging new technology, process and tools, enterprises can now achieve 40-50% Intelligent Automation related to SOX Compliance activities.
Click here for the full story.
2020 Blog, Blog, Featured
Many organizations include the assessment of fraud risk as a component of the overall SOX risk assessment and Compliance plays a vital role.
The word SOX comes from the names of Senator Paul Sarbanes and Representative Michael G. Oxley who wrote this bill in response to several high-profile corporate scandals like Enron, WorldCom, and Tyco in United Station. The United States Congress passed the Sarbanes Oxley Act in 2002 and established rules to protect the public from the corporates, doing any fraudulent or following invalid practices. Primary objective was to increase transparency in the financial reporting by corporations and initialize a formalized system of checks and balances. Implementing SOX security controls help to protect the company from data theft by insider threat and cyberattack. SOX act is applicable to all publicly traded companies in the United States as well as wholly owned subsidiaries and foreign companies that are publicly traded.
Compliance is essential for an organization to avoid malpractices in their day to day business operations, during these unprecedented times of challenge change such as what we are experiencing today. There are a lot of changes in the way we do business during the times of COVID. Workplaces have been replaced by home offices due to which there are challenges to enforce Compliance resulting in an increased risk of fraud.
Given the current COVID-19 situation while many employees are working from home or remote areas, there is an increased challenge of managing resources or time. Being relevant to the topic, on user provisioning, there are risks like, identification of unauthorized access to the system for individual users based on the roles or responsibility.
Most organization follow a defined process in user provisioning like, sending a user access request with relevant details including:
- User name
- User Type
- Application
- Roles
- Obtaining line manager approval
- Application owner approval
And so on, based on the policy requirement and finally the IT providing an access grant. Several organizations have been still following a manual process, thereby causing a security risk.
The traditional way of processing a user provisioning request, especially during the time of COVID-19 has become complicated. This is due to shortage of resources or lack of resource availability to resolve a task. Various reasons are:
- Different time zone
- No back-up resources
- Change in business plan
- Change in priority request
In such a situation automation plays an important role. Automation has helped in reduction of manual work, labor cost, dependency/ reliance of resource and time management. An automation process built with proper design, tools, and security reduces the risk of material misstatement, unauthorized access, fraudulent activity, and time management. Usage of ServiceNow has also helped in tracking and archiving of evidence (evidence repository) essential for Compliance. Effective Compliance results in better business performance.
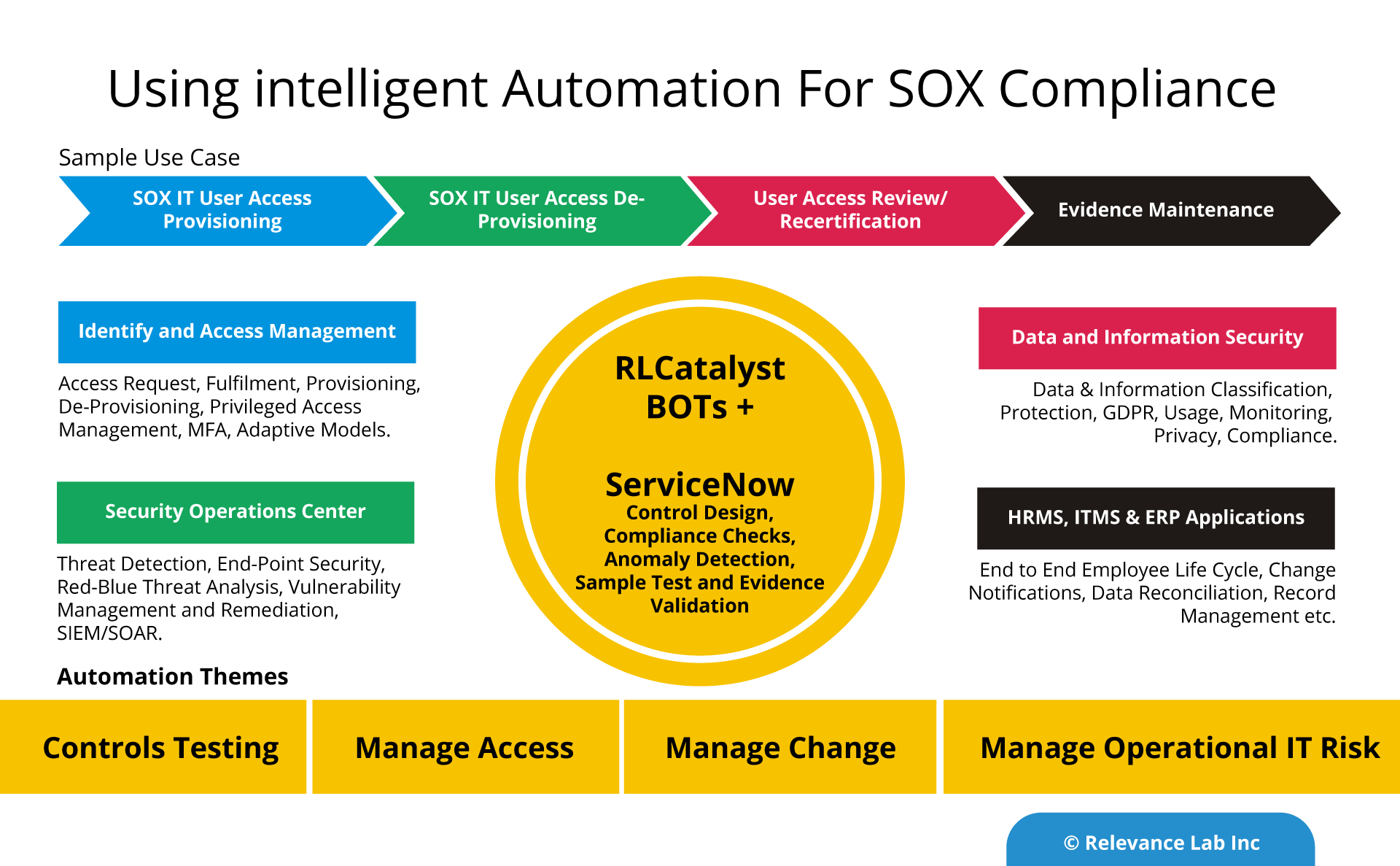
Intelligent Automation for SOX Compliance can bring in significant benefits like agility, better quality and proactive Compliance. The below table provides further details on the IT general controls.
Example – User Access Management
| Risk | Control | Manual | Automation |
|---|---|---|---|
| Unauthorized users are granted access to applicable logical access layers. Key financial data / programs are intentionally or unintentionally modified. | New and modified user access to the software is approved by authorized approval as per the company IT policy. All access is appropriately provisioned. | Access to the system is provided manually by IT team based on the approval given as per the IT policy and roles and responsibility requested.
SOD (Segregation Of Duties) check is performed manually by Process Owner/ Application owners as per the IT Policy. |
Access to the system is provided automatically by use of auto-provisioning script designed as per the company IT policy.
BOT checks for SOD role conflict and provides the information to the Process Owner/Application owners as per the policy. Once the approver rejects the approval request, no access is provided by BOT to the user in the system and audit logs are maintained for Compliance purpose. |
| Unauthorized users are granted privileged rights. Key financial data/programs are intentionally or unintentionally modified. | Privileged access, including administrator accounts and superuser accounts, are appropriately restricted from accessing the software. | Access to the system is provided manually by the IT team based on the given approval as per the IT policy.
Manual validation check and approval to be provided by Process Owner/ Application owners on restricted access to the system as per IT company policy. |
Access to the system is provided automatically by use of auto-provisioning script designed as per the company IT policy.
Once the approver rejects the approval request, no access is provided by BOT to the user in the system and audit logs are maintained for Compliance purpose. BOT can limit the count and time restriction of access to the system based on the configuration. |
| Unauthorized users are granted access to applicable logical access layers. Key financial data/programs are intentionally or unintentionally modified. | Access requests to the application are properly reviewed and authorized by management | User Access reports need to be extracted manually for access review by use of tools or help of IT.
Review comments need to be provided to IT for de-provisioning of access. |
BOT can help the reviewer to extract the system generated report on the user.
BOT can help to compare active user listing with HR termination listing to identify terminated user. BOT can be configured to de-provision access of user identified in the review report on unauthorized access. |
| Unauthorized users are granted access to applicable logical access layers if not timely removed. | Terminated application user access rights are removed on a timely basis. | System access is de-activated manually by IT team based on the approval provided as per the IT policy. |
System access can be deactivated by use of auto-provisioning script designed as per the company IT policy.
BOT can be configured to check the termination date of the user and de-active system access if SSO is enabled. BOT can be configured to deactivate user access to the system based on approval. |
The table provides a detailed comparison of the manual and automated approach. Automation can bring in 40-50% cost, reliability, and efficiency gains. The maturity model requires a three step process of standardization, tools adoption and process automation.
For more details or enquires, please write to marketing@relevancelab.com
Provisioning of complex and hybrid-cloud infrastructure setups. Click here for the full story.
2020 Blog, AIOps Blog, Blog, Featured
With growing Cloud adoption and need for Intelligent Infrastructure Automation, larger enterprises are adopting Hybrid-Cloud solutions like Terraform. Creating reusable templates for provisioning of complex infrastructure setups in Cloud and Data Centers, Orchestrating Cloud management with self-service Portals and full lifecycle monitoring of the assets can provide a flexible, reusable and scalable enterprise cloud solutions.
Relevance Lab is a Hashicorp partner with multiple successful enterprise infrastructure automation implementations using Terraform covering AWS, Azure, VMWare and GCP with 5000+ nodes setups.
Solution Highlights:
- Our solution allows you to rebuild stacks using automation completely. It is instrumental in provisioning newer environments with minimal code changes.
- It has the built in ability to replicate stacks across multiple regions with minimal code changes.
- Capability to add / remove new instances to components with few code changes.
- Simple code structure. Any new infrastructure needs can be easily provisioned by modifying the variables.
- Ability to modify instances such as Volumes, Instance Sizing, AMI changes, Security groups with minimal code changes.
Tools & Technologies:
Terraform from HashiCorp has emerged as the best Infrastructure automation tool. Terraform helps in building, changing and versioning of the infrastructure efficiently. Terraform is a declarative and, with the help of configuration files, we can describe the components to be built and managed across the entire datacenter.
Design Considerations:
Below mentioned are some of our design considerations based on standard practices in infrastructure automation. These structures have helped us gain flexibility and ease in scaling stacks based on demand.
- Code Repo Structure:
- It makes the code design structure very scalable to create newer AWS stacks in a different region or re-build stacks in case of a disaster or scale more resources based on traffic/load.
- A separate repo helps in maintaining isolation as each stack would have varied footprints of the resources.
- It helps in security and compliance as audits can be performed against a specific stack.
- Segmentation:
- Integration:
- Each change is performed on a branch which is merged via a Pull Request.
- Each Pull request is reviewed and verified and combined with the Master branch.
- Infrastructure changes are thoroughly tested during the PLAN stage and then terraform APPLY.
- Code reusability:
- Modules can help with this as they significantly reduce duplication, enable isolation, and enhance testability.
Each AWS stack is a separated GITHUB Repo while Terraform modules are a shared repo.
The below design model is showing the Automation build-out for each AWS account. Each layer is well segmented and can be easily scaled based on the needs. Making any specific change to each of the layers is easier.
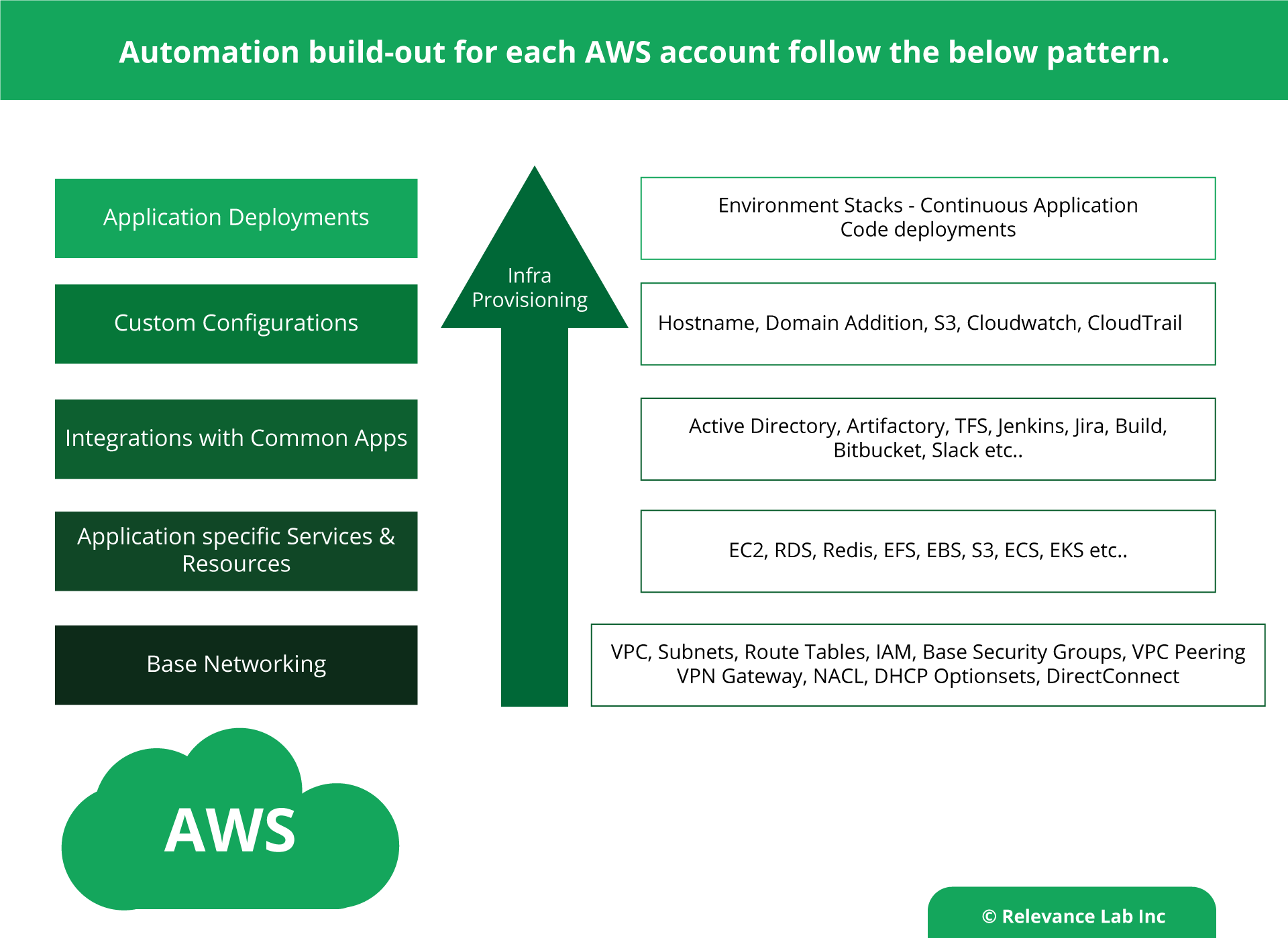
Fully integrated with GITHUB for Continuous Integration and Continuous Deployment.
Modules provide an easy way to abstract, common blocks of configuration into reusable infrastructure elements.
Benefits:
- Provides the ability to spin up an entire environment in minutes.
- It reduces time to rollout complex network and storage changes to less than a few minutes.
- Infrastructure is managed as a code, and all changes are tested well; resulting in fewer outages because of infra configuration changes.
- It is easy to operate and maintain because terraform uses a declarative language.
- Infra is Idempotent, and a state-based desired system.
Conclusion:
Using design best practices of terraform, enterprises can quickly build and manage infrastructure, which is highly scalable and efficient. Further, this automation can be hooked to a Jenkins pipeline project for automated code pushes for infra changes which can be tied to a standard release and deployment process.
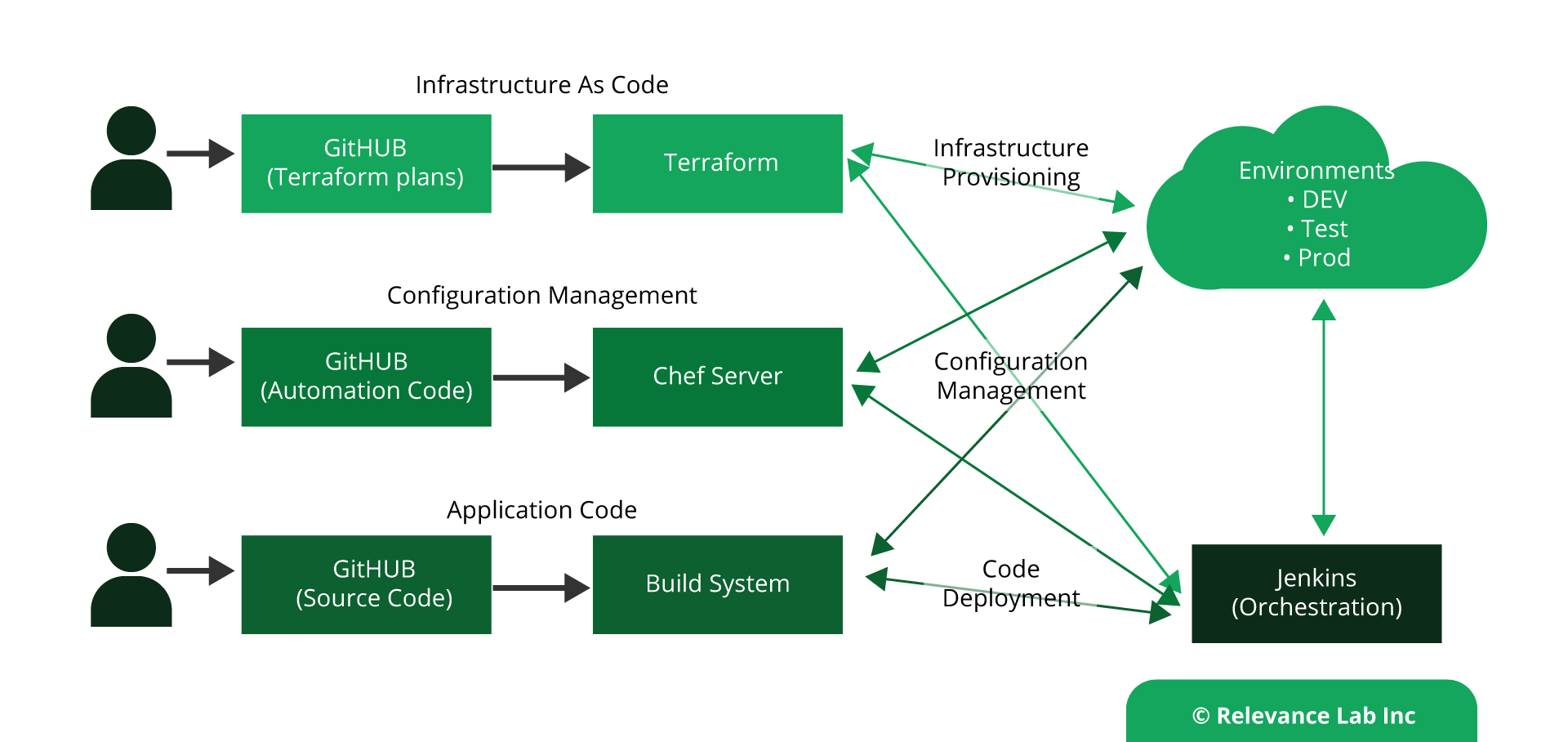
- Leveraging Chef for configuration management and managing all the application software installation and configurations via Chef cookbooks and recipes.
- Leveraging InSpec for auditing the properties of the AWS resources.
There are few other additions which could be introduced to this design to do a tight bonding between security and compliance policies and infrastructure as code. That may be achieved by integrating with Sentinel It helps in prevention of infra provisioning if there are deviations in the Infra code which do not adhere to the security policies. Sentinel helps us in building a fine-grained, condition-based policy framework.
For more details or enquires, please write to marketing@relevancelab.com
RLCatalyst now supports OKTA integration with SAML 2.0 for enterprise deployments.
Click here for the full story.
2020 Blog, Blog, Featured
RLCatalyst OKTA Integration
Modern Identity and Access Management are foundational to building digital customer experiences. In the area of Intelligent Automation, it is a critical need to have a proper authentication & authorization system and audit trail for BOT led executions. As BOTs handle more workload and user interactions, there is a crucial need to have RLCatalyst BOTs integrated with enterprise IDAM platforms like OKTA using SAML 2.0. OKTA provides a modern platform for IDAM and further by using SAML 2.0 adapter RLCatalyst now supports more secure and flexible security for both UI and API based access to its automation functionality. Our solution provides frictionless integration between ServiceNow, OKTA, Windows AD, RLCatalyst BOTs Server hosted across Hybrid Cloud platforms.
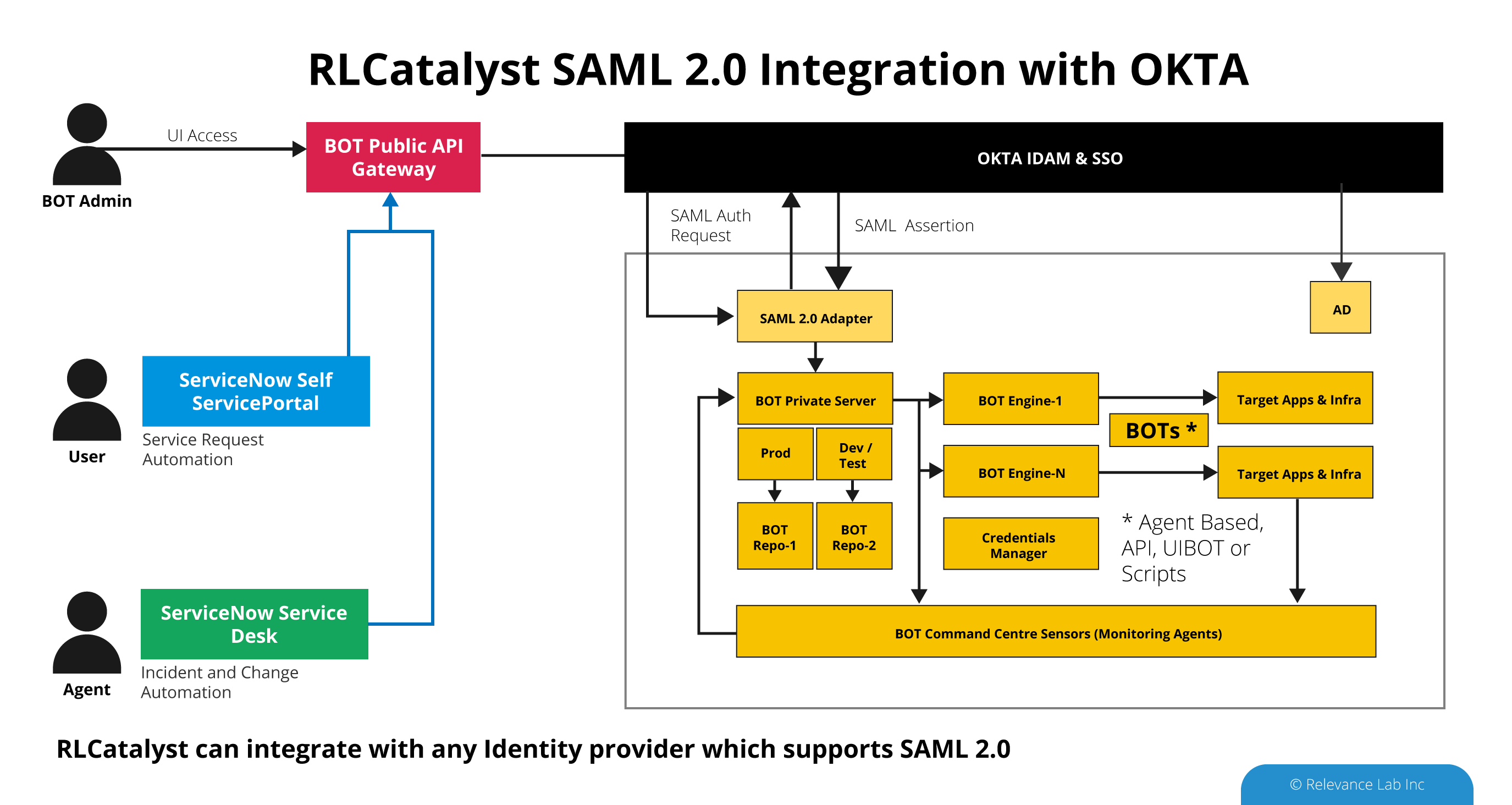
SAML 2.0 is a widely accepted industry standard for user authentication. It separates authentication and authorization from the application and the system of record for users which in most organizations is Active Directory or any LDAP based system. SAML 2.0 standard defines two entities. The first entity is the Identity Provider (IdP) to which applications can request authentication for a user. The other entity is the application itself (Service Provider or SP). Using applications integrated to IdP using SAML 2.0, users in an organization only need to have one set of credentials to log in to any application. Therefore, administrators can centrally administer access to all applications.
RLCatalyst BOTs Server is an Intelligent Automation software that is in use with enterprises and supports single sign-on using the SAML 2.0 protocol. When a user tries to access the application, they will be redirected to the Identity Provider’s login screen. The IdP accepts the credentials and authenticates the user and then redirects the user back to the RLCatalyst (here the Service Provider or SP) with an Auth Token. The SP then provides access to the resource requested. In subsequent requests, the same auth token is passed by the user agent, and the SP validates the token against the IdP and then provides access to the resource.
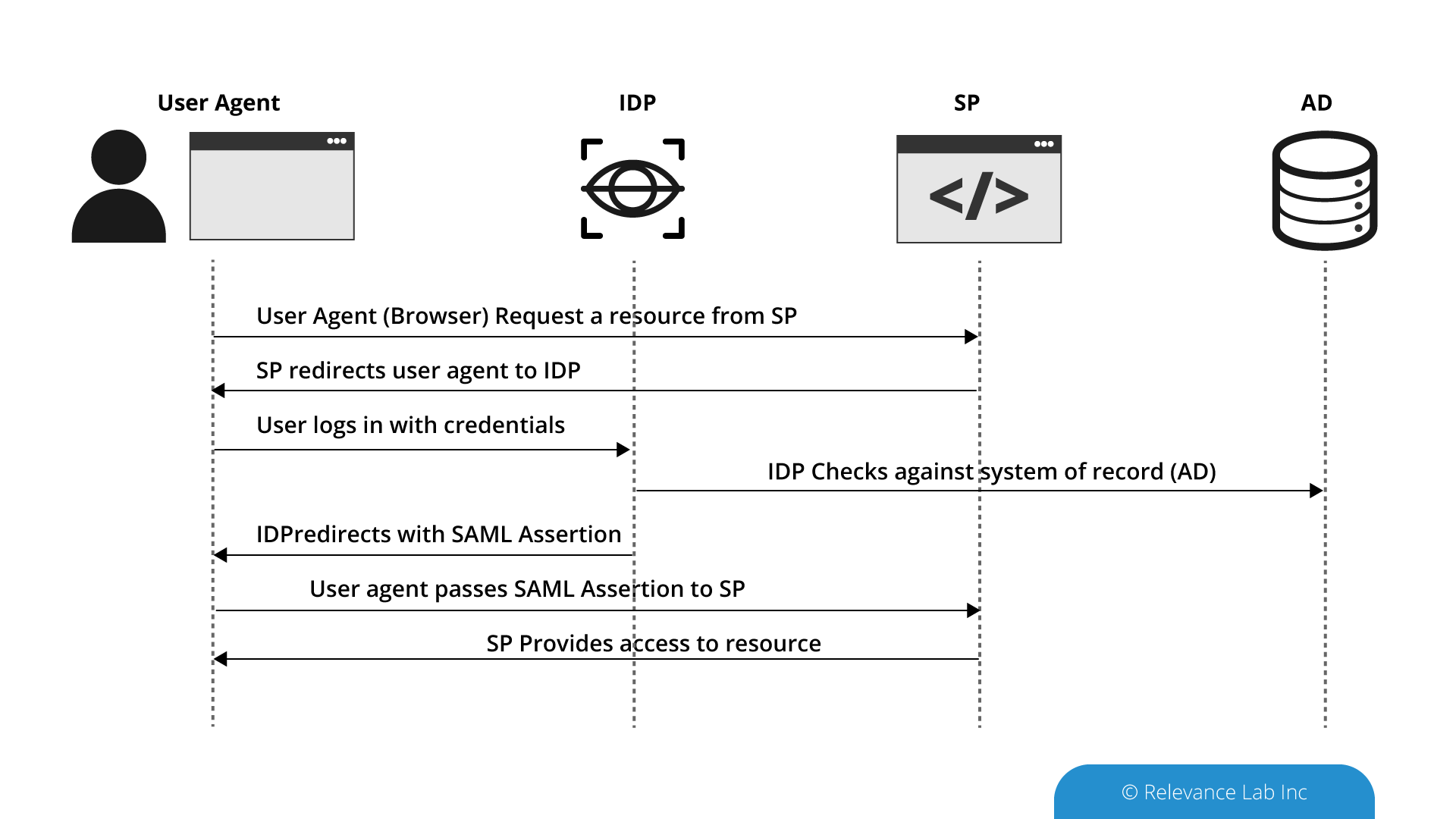
Supporting the SAML 2.0 standard allows RLCatalyst to seamlessly work with multiple Identity Providers like Okta, Auth0, Ping Identity etc. It enables enterprises to integrate our automation platform seamlessly into their SSO roll-out plans, thus reinforcing their security and compliance.
For more information feel free to contact marketing@relevancelab.com
