2023 Blog, ServiceOne, Blog, Featured
Automated Patch Management with Dynamic Insights
Relevance Lab helps customers use cloud “The Right Way” with an Automation-First approach as part of our Governance360 solution offering. Customers implementing this solution go through a maturity model covering the following stages:
- Basic Governance using AWS best practices with Control Tower, Security Hub, Management & Governance Lens
- Advanced Governance with automation-led approach and deep integration with service management tools, vulnerability assessment, and remediations
- Proactive and Preventive Governance with integrated end-to-end monitoring
- Intelligent compliance with remediations
As part of achieving this maturity model, it is important to have proper IT asset management, vulnerability assessment, and remediation models. A critical aspect of addressing infrastructure-level vulnerabilities depends on a smart patch management process. Patch management is a key part of your IT Operations to avoid potential exploitation and to ensure vulnerabilities are addressed on time by patching your systems, which includes operating systems, applications, and network components across your on-premises, cloud, or a hybrid setup.
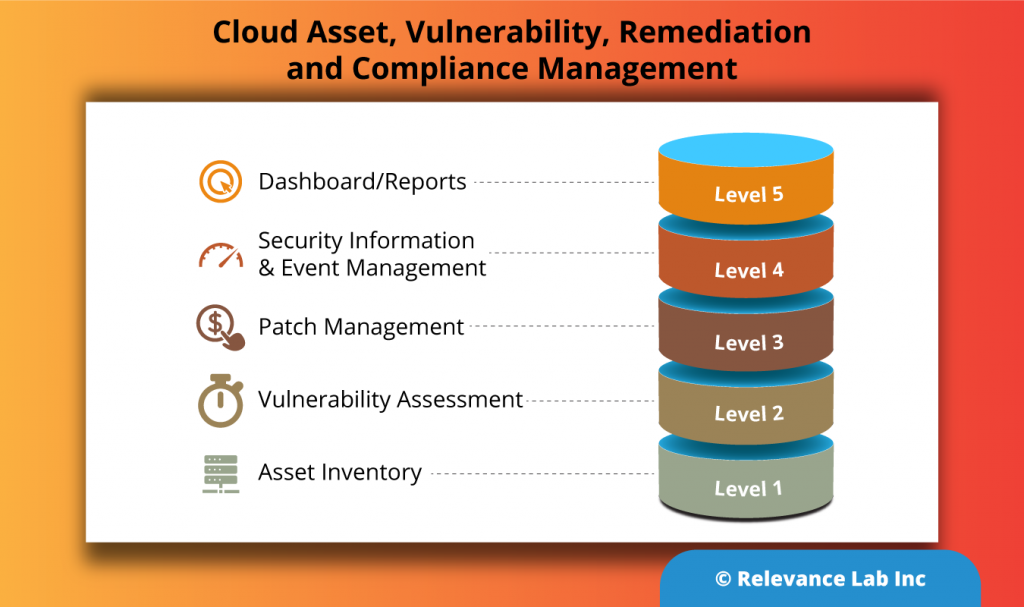
As shown below, patch management is a pivotal layer of security management and starts with the identification of assets from your asset inventory, followed by vulnerability assessment, patch management, security information & event management (SIEM), and visualization in the form of dashboards/reports.
Let us see the steps to automate the entire lifecycle of patch management as shown in the below picture along with some industry-standard tools/platforms.
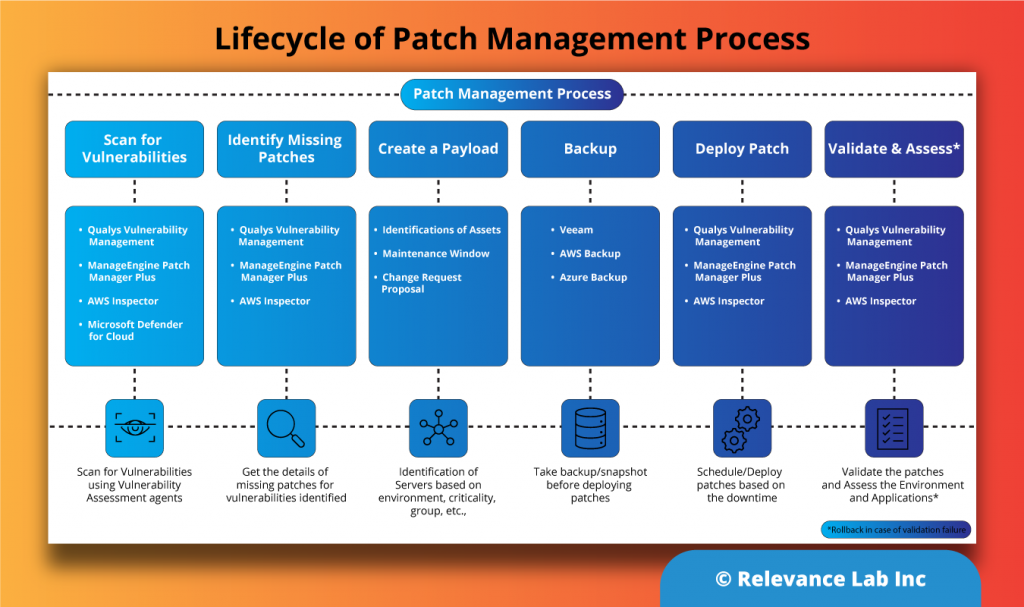
- Step 1: All vulnerabilities pertaining to operating systems and software are captured through periodic scans using agents and analyzed.
- Step 2: Using patching solutions, identify the missing patches and co-relate this to the vulnerabilities being addressed.
- Step 3: Based on the criticality of the servers like Dev, Test, Prod, or criticality of the patches, the assets are identified for patching. A Change Request (CR) is raised with the details of what to patch, along with the patching windows, and the asset owners.
- Step 4: Create a backup/snapshot before the patching activity and check for the patching client/agent availability on the servers planned for patching.
- Step 5: Patch the servers during the agreed window, and if successful, CR is updated accordingly. In case of failure, CR is updated with a failure status.
- Step 6: Post the patching activity, re-run the vulnerability scan to ensure all patch-related vulnerabilities are addressed and taken care of. The servers are also validated for the functionality of the applications before the CR can be closed.
Use Case Benefits for Customers
By automating patch management, customers can have near real-time visibility to the security compliance of their infrastructure and ensure an ongoing periodic process of patching is enabled, and having a 360-view of their IT infrastructure using dashboards. Enabling automated patching can save a lot of time and resources.
Compliance Benefits:
- Secured and centralized way of monitoring dashboard
- Automated patching
- Optical consistency across all businesses
- Providing ease of security auditing
- Periodic & timely notifications of the compliance/non-compliance status report to IT teams or individuals
The IT team can create their own custom patch baselines and decide which patches to auto-approve by using the following categories.
- Operating Systems: Windows, Amazon Linux, Ubuntu Server, etc.
- Product Name: e.g. RHEL 6.5, Amazon Linux 2014.089, Windows Servers 2012, Windows Server 2012 R2, etc.
- Classification: Critical updates, security updates, etc.
- Severity: Critical, important, etc.
Use Case of Hybrid Setup Patch Management
As shown in the sample below, there are 2 environments Prod, and Dev, referred to as Patch Groups. This helps to avoid deploying patches to the wrong set of instances. A patch group must be defined with the tag key Patch Group. For example, we have created a patch group tag key called Dev below. A fleet of instances that have these tags can be patched using this approach.
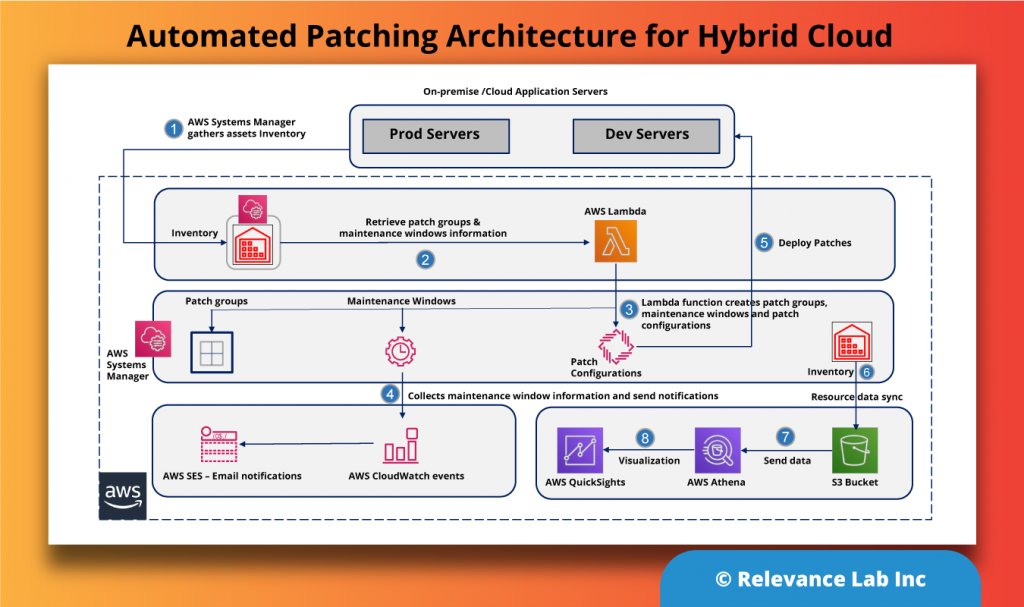
Details of the Architecture
- AWS Systems Manager gathers asset inventory details and a pre-configured maintenance window automatically scans for the latest patches for the server groups at a scheduled time.
- The automated patch function lambda is scheduled to run daily to collect the patch group and maintenance window details. It also creates the patch group and maintenance schedule tags on the managed instances.
- This lambda function then creates or updates the right patch groups and maintenance schedules, associates the patch groups with the patch baselines, configures the patch scans, and deploys the patching task. You can also notify users of impending patches using CloudWatch Events.
- As per the maintenance schedule, the events will send patch notifications to the application teams with the details of the impending patch operation.
- Patch Manager then initiates the patching based on the predefined window and patch groups.
- Details about patching are retrieved using resources data sync in Systems Manager and published to a S3 bucket.
- Using this data from the S3 bucket, you can build a visualization dashboard about the patch compliance in Amazon QuickSight.
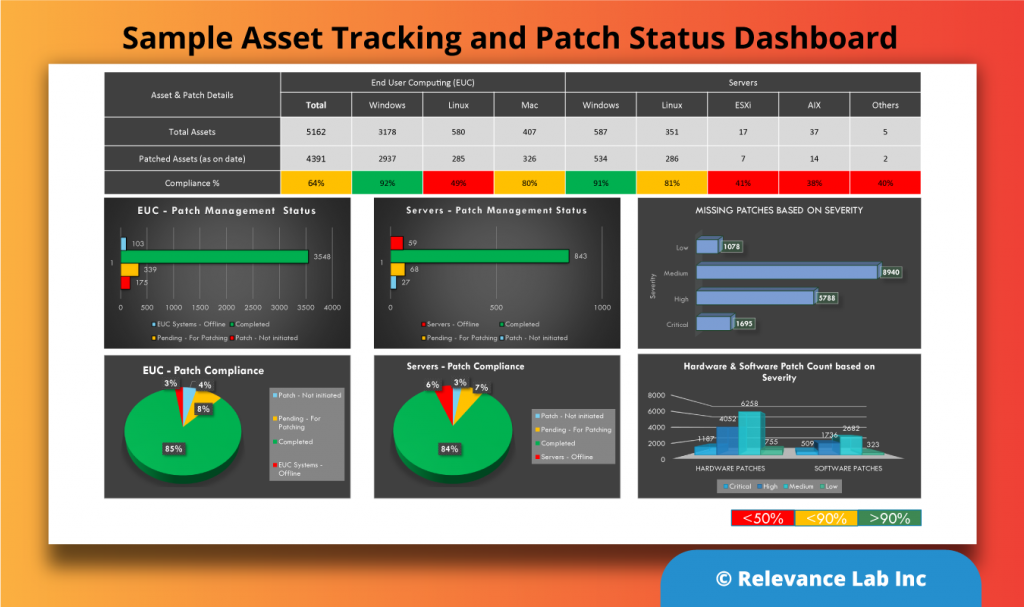
As explained earlier, visualization is an essential layer showing the near real-time security status of your IT infrastructure. These can be a dashboard, as shown below.
Getting Started
Patch Management is available as a professional service offering and also as an AWS marketplace offering under Governance360. Below are the steps to take the customer from discovery to steady state.
| Step-1 | Discovery | Assess the current landscape of Process & Tools/Technology |
| Step-2 | Recommend | Present the current gaps and benchmark against industry standards |
| Step-3 | Plan and Implement | Design and implement the proposed solution in a phased manner |
| Step-4 | Ongoing | Bring the solution to a stable state/BAU (Business As Usual) |
Conclusion
In this blog post, we covered the key aspects of automated patch management for enterprises. Relevance Lab has implemented automated patch management solutions, which is part of our Automation Factory Suite for its key customers bringing in better detection, assessment and compliance for their Cloud Governance. The entire solution is available as a re-usable framework that can save new enterprises 6+ months of time, efforts and costs for new deployments.
To know more about our Governance360 offering and its building blocks, including automated patch management, feel free to contact marketing@relevancelab.com.
References
Automated Patch Management for Cloud & Data Centers


